via Gizmodo investigative reporter Dell Cameron, comes the astounding news of the systemic incompetence in properly handling secret documents and other artifiacts stored within the cloud (in this case, AWS S3 Buckets) by a well established contractor to the National Geospatial-Intelligence Agency (NGA). Certainly, a first-rate example of an Expanding Cloud of Lethal Stupidity (ECOLS).
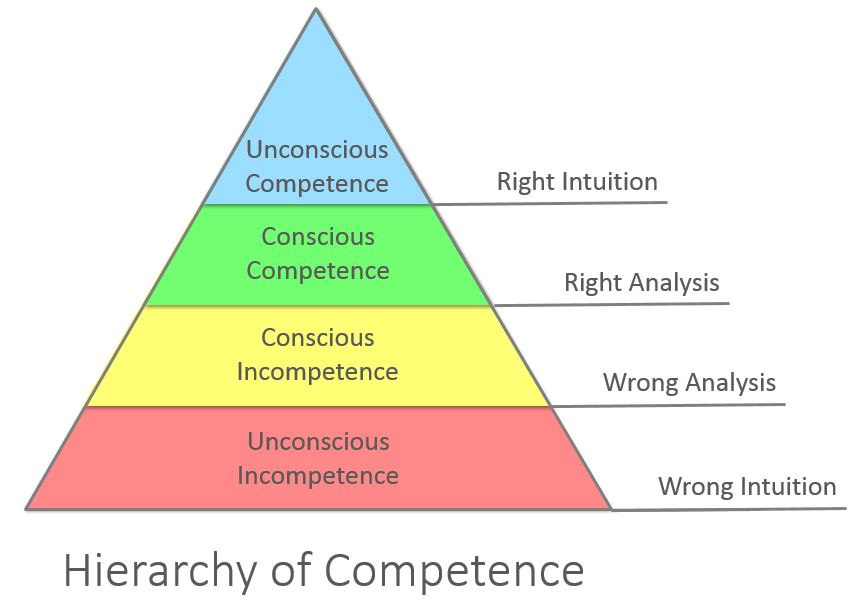
Where does the organization in question fall within the Noel Burch Hierarchy of Competence model?. Should the culprits in this scenario be prosecuted? You be the judge. Truly astounding, indeed.
"A cache of more than 60,000 files was discovered last week on a publicly accessible Amazon server, including passwords to a US government system containing sensitive information, and the security credentials of a lead senior engineer at Booz Allen Hamilton, one of the nation’s top intelligence and defense contractors. What’s more, the roughly 28GB of data contained at least a half dozen unencrypted passwords belonging to government contractors with Top Secret Facility Clearance." - via Gizmodo reporter Dell Cameron