Forbidden Research - Snowden's MIT →
Anti-espionage bombast? Nothing more than diatribe-like vaporware? You be the judge...
Anti-espionage bombast? Nothing more than diatribe-like vaporware? You be the judge...

Newly revealed discovery of coil whine exploitation, targeting the harvesting of cryptographic artifacts (in this case, keys) via wireless connectivity. More here.

Well wrought thought piece on the use, and misuse, of prepaid cellular telephony hardware, the so-call Burner, and the effort to enforce regulations thereto. Entitled Burner Phones: Will Tightening Restrictions on Prepaid Cell Phones Solve Anything? Certainly today's Must Read post...
The Electronic Frontier Foundation has published an interesting look at secure messaging, as it exists today, including a super-handy scorecard. Yay!
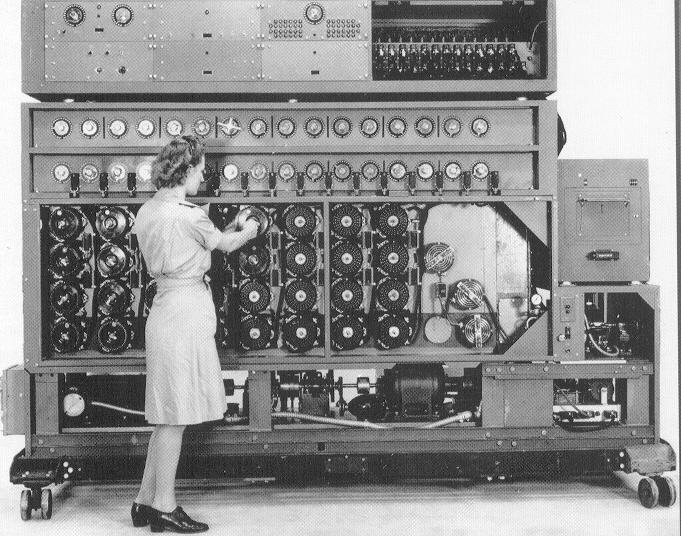
Bletchley Park pays homage to the popularly monikered Bombe Girls (Eight Wrens - Women’s Royal Naval Service), who had arrived at Bletchley Park seventy five years go, and focused on operating the Turing-Welchman Bombe Machine.

Interesting post at NODE, proffering advice to 中本哲史 Nakamoto Satoshi on the method to attain the penultimate viral outcome. Bitcoin users, rejoice...


Ars Technica's Megan Geuss reports the apparent defeat of security technologies associated with so-called 'secure chip-and-pin' credit cards. Today's Must Read.

Google, Inc. (NasdaqGS:GOOG) has warned Symantec Corporation (NASDAQ:SYMC) of imposed requirements applied to the Symantec Certificate Authority due to apparent malfeasence in managing the company's Certificate Authority infrastructure and specifically Certificates issued without notifying the holders of same.
The implications of the action are range far both in scope (related to the specific certificates under scrutiny ("Symantec performed another audit and, on October 12th, announced that they had found an additional 164 certificates over 76 domains and 2,458 certificates issued for domains that were never registered. - posted by Ryan Sleevi, Software Engineer at Google, Inc.)), and in Google's efforts to enforce the WebTrust in the Digital Certificate realm. This is why I say, Trust - But Verify...
"It’s obviously concerning that a CA would have such a long-running issue and that they would be unable to assess its scope after being alerted to it and conducting an audit. Therefore we are firstly going to require that as of June 1st, 2016, all certificates issued by Symantec itself will be required to support Certificate Transparency. In this case, logging of non-EV certificates would have provided significantly greater insight into the problem and may have allowed the problem to be detected sooner." - Posted by Ryan Sleevi, Software Engineer at Google, Inc.

Interesting source this time, coming from Roger Fingas, writing for Apple Insider, detailing the current Lame-Duck Administrations' decision to avoid forcing corporate entities to decrypt communications for Law Enforcement Agencies.

Litany of the quiet heroism of William Gordon Welchman at Bletchley Park, his modern day connections (in this case his granddaughter's well-placed esteem). Today's Must Read.

In a well-engineered screed, targeting both laptop and phone encryption modalities, Andrew Cunningham writing at Ars Technica's gadget section provides us with a tell-all discussion of how, in fact, to protect thyself from the evil that lurketh without. Today's Must Read.