Rooting
via Ax Sharma - writing at Bleeping Computer, comes the tale of the unc0ver jailbreak flaw on all versions of Apple Inc.'s (NASDAQ: AAPL) iOS mobile operating systems - now at version 13.5.1. Today's Must Read.
via Ax Sharma - writing at Bleeping Computer, comes the tale of the unc0ver jailbreak flaw on all versions of Apple Inc.'s (NASDAQ: AAPL) iOS mobile operating systems - now at version 13.5.1. Today's Must Read.
Ladies and Gentlemen, Girls and Boys: The Redmondian Leviathan
via the inimitable Lawrence Abrams, writing at Bleeping Computer, comes the bad news for Microsoft Corporation (NASDAQ: MSFT) and Windows users worldwide. The latest Zero Day IE fix has apparently broken printing for a large number of users of the Windows operating system. What has happended to the once highly respected QA groups at the Redmondian Leviathan? Read more...
'On January 17th, 2020, Microsoft disclosed a zero-day remote code execution vulnerability in Internet Explorer 11, 10, and 9 that was being used in "limited targeted attacks". As no update is available yet, Microsoft released a temporary fix that involves changing the owner of the %windir%\system32\jscript.dll and denying access to the file for the Everyone group.' - via Lawrence Abrams, writing at Bleeping Computer
Image Courtesy of Brian Smale and Microsoft
Why is Microsoft Corporations' (NASDAQ: MSFT) CEO Satya Nardella touting underwater servers instead of focusing on the plight of current Windows Server and Desktop users dealing with the apparent incompetence of Microsoft staff and contractors running Windows Update systems? (With the latest screwup in Windows Update-land - the bad code pushed out to users in the October 2018 Update that deleted user files, and other necesary system files - is as of today NOT not fixed which caused the company to pull the October Update - and it's now November...) Is it the money from the cloud profit center (otherwise known as Azure) that's 'clouding' his vision? You be the judge!
Via Dan Goodin, Security Editor at Ars Technica, comes news of OpenBSD, Debian, CentOS, Ubuntu and Red Hat Linux flaws - in existence for an estimated 23-months (and just discovered).
'An advisory X.org developers published Thursday disclosed the 23-month-old bug that, depending on how OS developers configure it, lets hackers or untrusted users elevate very limited system rights to unfettered root.' - via Dan Goodin, Security Editor at Ars Technica
Image Credit: Microsoft Corporation
Smart Move - Satya - Smart Move Now, what was it you were going to do about the October Creators Update for Windows 10 nagging problem of deleting user documents and other files en mass? Was this a redirection marketing tactic to deflect attention from the recent rash of Microsft Windows Update failures plaguing Redmond; or is it a Lack of Focus Mr. Nadella? (Update: News from Martin Brinkmann at GHacks that the file deletion issue is reportedly fixed). To be fair, an inability to service operating system updates robustly is not just a Microsoft Corporation (Nasdaq: MSFT) failure, this SNAFU is a hallmark of the so-called Android 'ecosystem' as well. Oh, and I'm a cricket fan as well. Enjoy.
via the inimitable Rich Mogull, writing at TidBits, comes this interesting take on newly implemented user-land security operability problems in Apple Inc.'s. (Nasdaq: AAPL) desktop operating variant of Darwin (aka macOS X (10.14 Mojave). Typically, strict utilization of user-land intervention implementing security controls leads to insecure configurations. Today's Must Read (especially considering the mew macOS version is due for general release today!).
Roy Iarchy, writing at Symantec's security blog, comes this story of Apple Inc.'s (Nasdaq: AAPL) iOS, Operating System flaws, and the vector - the TrustJacking gambit, all wrapped up in a nice tidy package. Bad news for iOS, good news for Security vendors, eh? And, not surprisingly, users running older devices not patchable by APple are vulnerable to this form of iOS device jacking as Apple's not focused on patching older devices. Today's unfortunate Must Read.
Vice's Motherboard scribe Lorenzo Franceschi-Bicchierai regales us (on a Monday, no less), of the tale of monetary gains in the world of high-end Apple Inc. (NasdaqGS: AAPL) iPhone bugs. In this case, where, in fact, the real money resides. Today's Must Read.
Well-wrought thought piece on the failure of Red Hat and Ubuntu to secure their respective distros utilizing standardization in the form of reproducible builds (and other means).
Damn kids apparently have forgotten their lessons whilst in kindergarten regarding safe and fair play. In this case, however, we have the added component of organizations, companies and individuals suffering due to the ineptitude of the big names in Linux... Astounding.
News of two (SAMRi10, NetCease) Microsoft Corporation (NasdaqGS: MSFT) PowerShell scripts from Itai Grady providing at least some preventative Windows 10 medicine in the on-going battle against Windows Cruft.
via ZDNet's Charlie Osborne comes a well-wrought report of the continued unremediated and unmitigated flaws in Microsoft Corporation's (NasdaqGS: MSFT) Windows 10.
J.M. Porup - an Ars Technica UK writer - examines the security posture of the Linux kernel, and finds it somewhat wanting...

Meanwhile, in Microsoft Corporation (NASDAQGS: MSFT) news, comes this piece from BGR; focusing on the EFF's targeting of the Redmond, WA leviathan's allegedly egregious use of Windows Update to push Windows 10 onto user's desktops... Visit the Electronic Frontier Foundation's blog for more info.

Microsoft Corporation (NasdaqGS: MSFT) has released the Redmond, Washington software leviathan's Privileged Access Workstations.
Essentially, PAWS provisions a workstation to perform high risk-determined activities (SysAdmin work, for example), and permits a user VM on the machine to perform less sensitive, mundane tasks such as normal office tasks.
Seems a might crufty, eh?
'In simplest terms, a PAW is a hardened and locked down workstation designed to provide high security assurances for sensitive accounts and tasks. PAWs are recommended for administration of identity systems, cloud services, and private cloud fabric as well as sensitive business functions.' - via Microsoft Technet
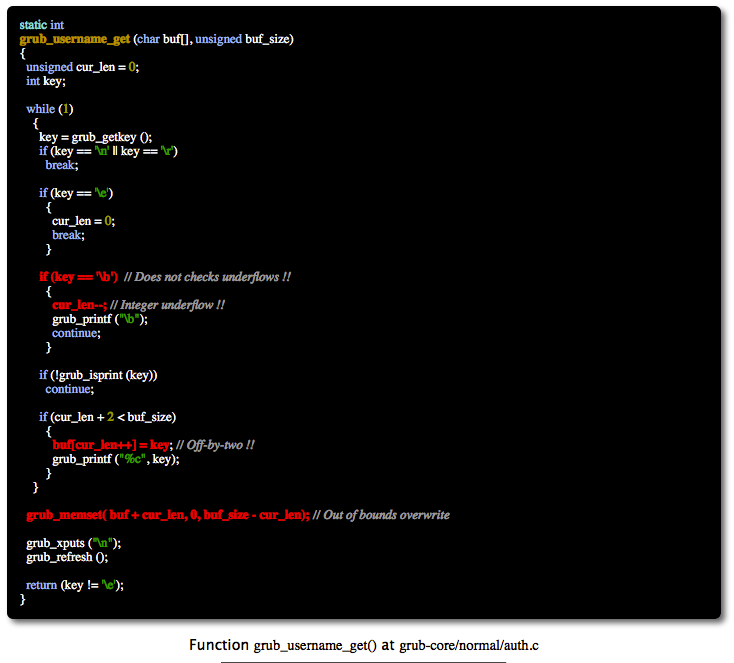
Old, as these things go, yet truly the most glaring example of operating system failures yet seen, this time in Linus's Linux (Full Disclosure: We are heavy users of at least three Linux distro's)... Comes this outstandling and outrageous vulnerability, starting in 2009's release of Grub (also known as the Grand United Bootloader) all the way down through the ages to today 2015! The Dr's Marco and Ripoll of this embroglio-laden code expound further:
"A vulnerability in Grub2 has been found. Versions from 1.98 (December, 2009) to 2.02 (December, 2015) are affected. The vulnerability can be exploited under certain circumstances, allowing local attackers to bypass any kind of authentication (plain or hashed passwords). And so, the attacker may take control of the computer. Grub2 is the bootloader used by most Linux systems including some embedded systems. This results in an incalculable number of affected devices." - via Hector Marco, Ph.D. & Professor Ismael Ripoll, Ph.D., Cybersecurity Group.

"The consequences of such attacks are devastating, leading to complete disclosure of the most sensitive user information (e.g., passwords) to a malicious app even when it is sandboxed," the researchers warned. "Such findings, which we believe are just a tip of the iceberg, will certainly inspire the follow-up research on other XARA hazards across platforms." - via Dan Goodin, writing at Ars Technica
News, of vulnerabilities discovered within the Bayerische Motoren Werke AG (XETRA: BMW AG) Connected Drive system, now in many BMW cars and SUVs. Specifics revolve about the capability for remote unlock, and the hack thereof.