Browser Cookie Jar: The Pilferage
via Cory Doctorow, comes this fascinating stoy of academicians exercising superlative research and detection skills in the effort to understand - in excrutiatingly intense detail - the true nature of cookie policies, in this case third-party cookie polices.
Entitled Who Left Open the Cookie Jar? A Comprehensive Evaluation of Third-Party Cookie Policies (PDF) (and of course, the researchers'documentation targeting the trove of discovered exploits) are all at your disposal to assit and perhaps discover other flaws in the browsers under scrutiny,
The creator/academians at the root of this ooutstanding comprehensive work - Gertjan Franken, Tom Van Goethem and Wouter Joosen all are Researchers at Catholic University in Leuven, Belgium were awarded the Distinguished Paper prize at this summers' Usenix Security Conference. Also covered in Academics Discover New Bypasses for Browser Tracking Protections and Ad Blockers by Catalin Cimpanu at Bleeping Computer. Both are today's Must Read!
Dr. Chuvakin's Prescription: 'On Negative Pressure ...'
via Anton Chuvakin, Ph.D., Research VP and Distinguished Analyst at Gartner, speaks security truth to power. Pay attention folks - your organization's security and continued existence could very well depend on the action you take in your environments, based what he has to say.
Sam Cattle on Ransomware →
DARPA, The Implantation Instantiation →
News, via the IEEE's Spectrum Magazine (and reported by Eliza Strickland) of a challenge from DARPA's Neural Engineering Systems Design; in this case, the need for a recording brain implant has been identified. Indeed.
Myctyris Longicarpus, Ratiocinor Infra Aedificium →
Via Futility Closet comes an outstanding computational methodology utilizing blue soldier crabs as the componentized logic delivery mechanism for a bio-computational device (in this case - a logic gate). Certainly today's MustRead.
The Origami Solution →
Meanwhile - admist all the foo-fa-raw of last weeks' RSAC 2017 - came very good physical security new's of a fascinating kevlar and aluminum origami-based ballistic shield (developed by Engineers at Brigham Young University) that stops .44 calibre magnum slugs. Very good news for law enforcement, and other organizations (think schools, other civilian government organizations, military, businesses)
The design is able to protect multiple people at one time and folds down to a compact shape. Utilizing the Yosimura Origami Crease Pattern, it currently tips the scales at a paltry 55 lbs. (25 kg).
Simply Outstanding.
Paul Vixie, Compromised Security in IoT Caused by Market Pressure →
via the Internet Society's blog, comes an outstanding screed - penned by Jeri Clausing - detailing the on-target cogitation of the eponymous Paul Vixie, Ph.D., this time, those thoughts encompass the in-built security flaws of the seemingly ubiquitous IoT infrastructure. Read it and Weep.
Soghoian, Your Smartphone is a Civil Rights Issue →
Dr. Soghoian's Take...
Tip O' The Hat to Firewall Consultants!
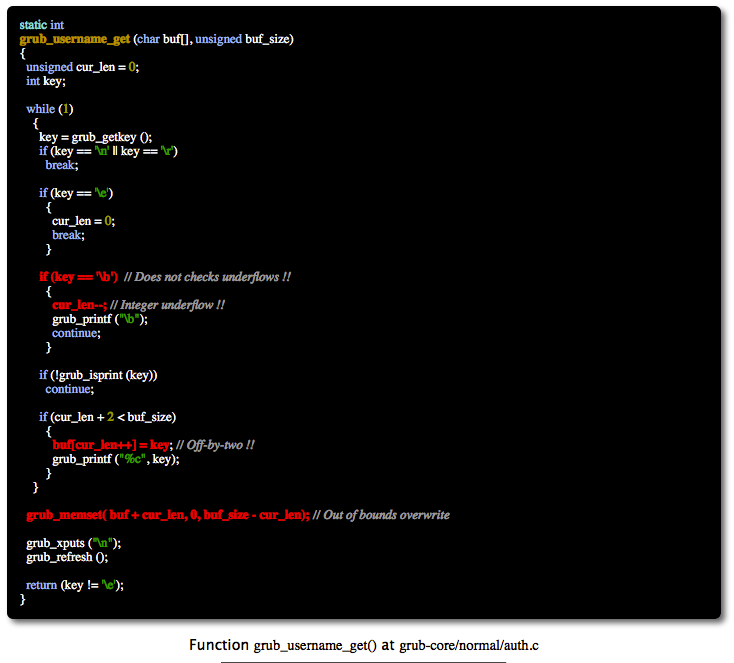
28x →
Old, as these things go, yet truly the most glaring example of operating system failures yet seen, this time in Linus's Linux (Full Disclosure: We are heavy users of at least three Linux distro's)... Comes this outstandling and outrageous vulnerability, starting in 2009's release of Grub (also known as the Grand United Bootloader) all the way down through the ages to today 2015! The Dr's Marco and Ripoll of this embroglio-laden code expound further:
"A vulnerability in Grub2 has been found. Versions from 1.98 (December, 2009) to 2.02 (December, 2015) are affected. The vulnerability can be exploited under certain circumstances, allowing local attackers to bypass any kind of authentication (plain or hashed passwords). And so, the attacker may take control of the computer. Grub2 is the bootloader used by most Linux systems including some embedded systems. This results in an incalculable number of affected devices." - via Hector Marco, Ph.D. & Professor Ismael Ripoll, Ph.D., Cybersecurity Group.